
Alok Menghrajani
Previously: security engineer at Square, co-author of HackLang, put the 's' in https at Facebook. Maker of CTFs.
This blog does not use any tracking cookies and does not serve any ads. Enjoy your anonymity; I have no idea who you are, where you came from, and where you are headed to. Let's dream of an Internet from times past.
Home | Contact me | Github | RSS feed | Consulting services | Tools & games
An ingenious phishing vector: Aza Raskin found a clever way to phish users’ credentials. The idea consits of waiting until a visitor switches tabs to replace the favicon and page content with a fake site.
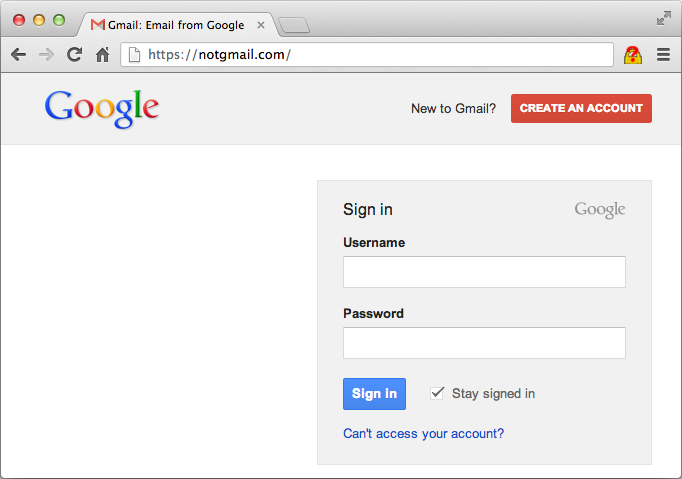
Proof of concept
You can try the attack by visiting http://www.azarask.in/blog/post/a-new-type-of-phishing-attack/. After loading the page, switch tabs for a few seconds and then go back to Aza’s site.
Mitigation
You can avoid falling for this attack by:
- Always checking the URL before entering a password.
- Closing tabs you no longer need.
- Using your browser’s account manager.
- Opening shady websites in a dedicated window, browser or laptop.